Last date modified: 2026-Feb-12
Register Purview Sync with Azure
Purview Sync uses the Microsoft Graph API. For more information on Microsoft Graph API, see Microsoft's documentation.
To access the API, you must register an application in Azure Active Directory. Authentication requires referencing a dedicated Azure AD application that has the necessary permissions. This configuration must be performed on the client side by an Azure user with sufficient administrative rights.
At different times in this guide, you will be instructed to take note of certain values and tokens. We recommend opening a text editor or Word document during this process to copy and paste these values, so they are readily available to paste into RelativityOne.
There are two ways to register Purview Sync application with Azure:
- Automated script. Run a PowerShell script as an Azure administrator. This script will create the app registration and configure all required permissions automatically.
- Manual setup. Sign in to the Azure portal as an administrator and complete the app registration manually, including assigning the necessary permissions.
The person completing the application registration process needs to be an Azure Administrator with sufficient privileges. Refer to Microsoft’s documentation for more details.
When registering the Purview Sync app in Azure:
- Authority URI specifies the Microsoft tenant that handles authentication. It ensures sign-in is processed by your organization’s trusted identity provider—Microsoft Entra ID.
- Redirect URI defines the secure endpoint where Microsoft sends the authentication response after sign-in. This allows Purview Sync to receive authorization tokens and complete the login process.
After completing the app registration process, whether automated or manual, collect the final values required for configuring RelativityOne Purview Sync. Store these values securely for future use. The following are examples of those values:
- Client ID: 1234567890abcdef1234567890abcdef
- Authority URI: https://login.microsoftonline.com/abcdef1234567890ab1234567890abcd
- Redirect URI: https://kcura.relativity.one/Relativity/CustomPages/4985c522-5931-41ba-bf67-7d58ee96e6d1/index.html
- Client Secret: w7X...<onlyshownonce>...
Automating Purview Sync registration in Azure Active Directory with a script
You can automate your Purview Sync registration in Azure Active Directory using the provided PowerShell script: PvS-MSFT-Automation-Script.ps1. After you run the script, the registration process will complete automatically. If your organization restricts script execution, check with your IT or Security team to ensure you have the required permissions.
Requirements
You must have the following before automating the Purview Sync registration:
- You must be an Azure AD Global Administrator.PowerShell 5.1+ with execution policy allowing local scripts.
- Internet access to login.microsoftonline.com and graph.microsoft.com.
- The script auto-installs Microsoft.Graph modules if missing. This requires install-module privileges.
Automating the registration
To register the app with the PowerShell script, follow the steps:
- Download the PvS-MSFT-Automation-Script.ps1 file.
- Open PowerShell Window.
- Run the following command. Change TenantRoot to your Relativity instance name and AppName to the name you want to use for the Azure App Registration.
.\PvS-preReq-v1.ps1 -TenantRoot "https://kcura.relativity.one" -AppName "RelativityOne Purview Sync" - After the script is run, copy the values from the PowerShell output to a safe location. You will need them to configure Purview Sync in RelativityOne later.
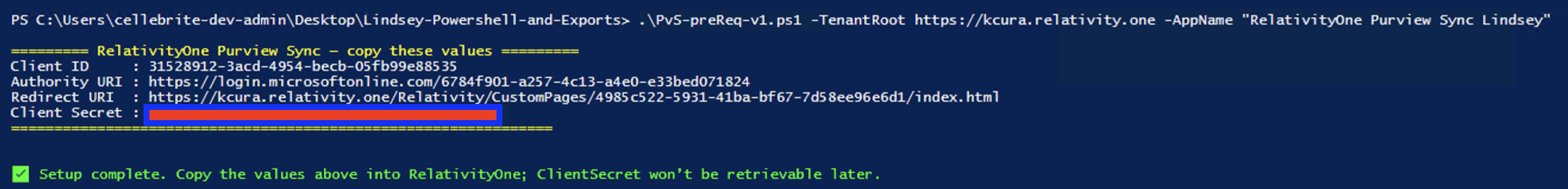
For more details, refer to the Community article RelativityOne - Purview Sync: Azure Active Directory Registration Script.
Registering an Azure application and credentials manually
Complete the steps in this section to create an app registration for email integration and syncing with Microsoft Entra ID.
To generate your Application (Client) ID and Client Secret, you must have Application Administrator privileges to sign in to the Azure portal and register the application. Store the Application ID and Client Secret securely, as you will need them in RelativityOne.
To register your app:
- Open your Azure Portal.
- Click Microsoft Entra ID.

- In the left-navigation menu, select App registrations.
- Click New Registration.
This will open the Register an application page.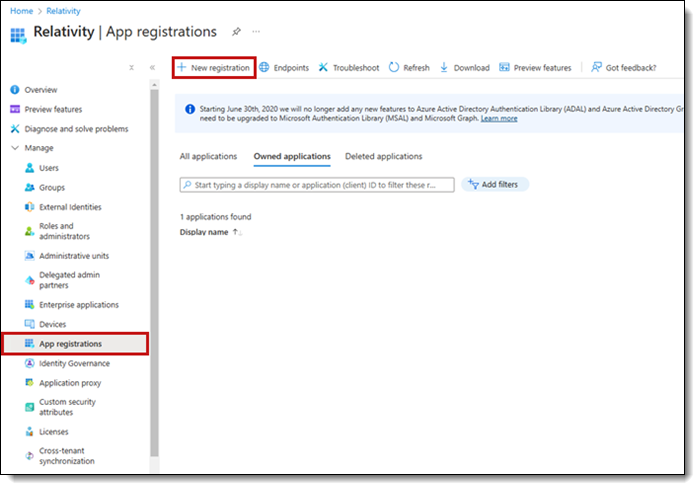
- Enter an application name in the Name field. For example, RelativityOne Purview Sync.
- Select Accounts in this organizational directory only - Single tenant as the supported account type.
- Select Single-page application (SPA) in the drop-down menu in the Redirect URI field.
- Enter https://[RelativityOne URL up to the word relativity forward slash] + CustomPages/ 4985c522-5931-41ba-bf67- 7d58ee96e6d1/index.html for the Redirect URI field. For example, https://company.relativity.one/Relativity/CustomPages/4985c522-5931-41ba-bf67-7d58ee96e6d1/index.html.
- Click Register.
When you complete the application registration, take note of the Application (client) ID field and Directory (tenant) ID field. These will be later used in Relativity.

Authentication
For authentication, you must add a redirect URI. This allows Purview Sync to receive authorization tokens from Microsoft and complete the login process.
To add a redirect URI:
- Select Authentication (Preview) from the left-side menu.
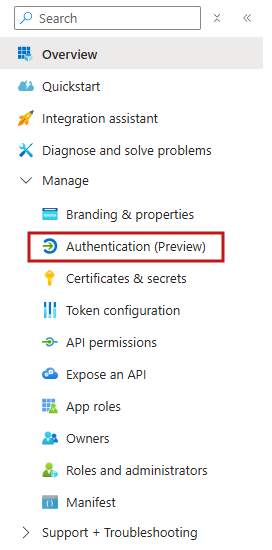
- Locate the Single-page application box and select Add URI.
- In the Redirect URI field, enter https://[RelativityOne URL up to the word relativity forward slash] + CustomPages/ 4985c522-5931-41ba-bf67-7d58ee96e6d1/ms-auth-popup-redirect.html. For example, https://company.relativity.one/Relativity/CustomPages/4985c522-5931-41ba-bf67-7d58ee96e6d1/ms-auth-popup-redirect.html.
- Locate the Web box and select Add URI.If you do not see the Web box, you need to create a new platform. Select Add Redirect URI and then select Web platform. Then, continue to step 5.
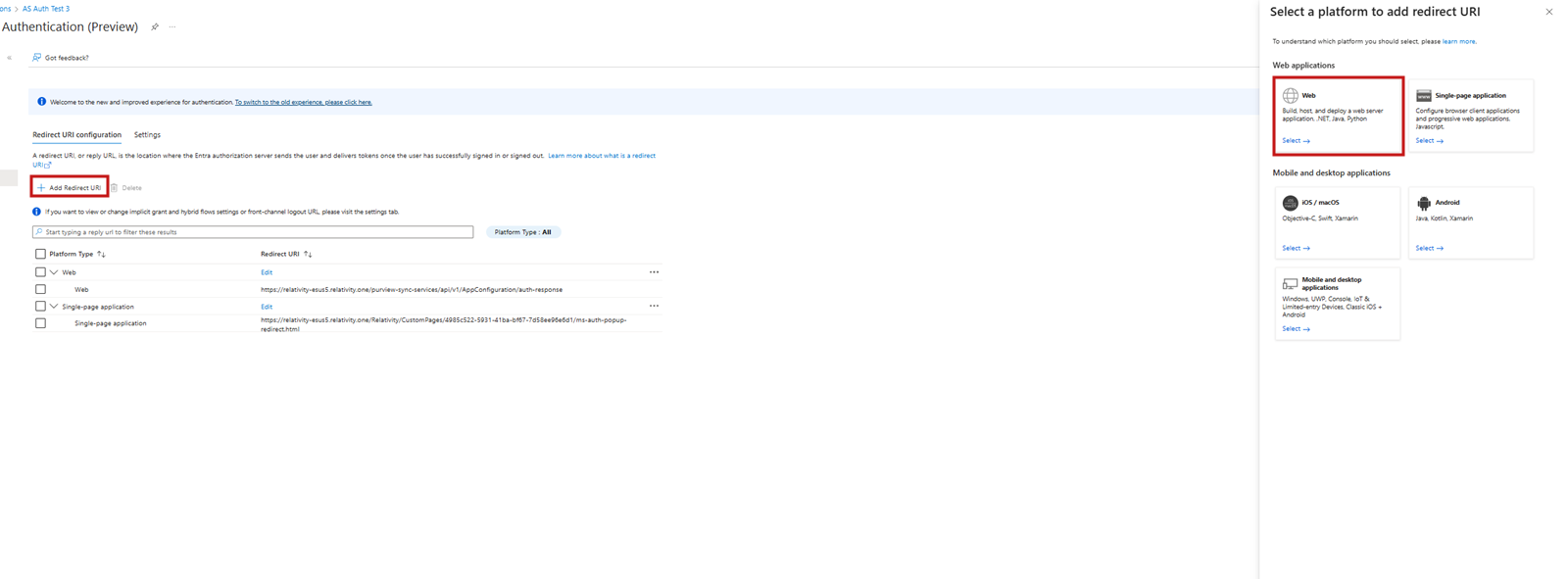
- In the Redirect URI field, enter https://[RelativityOne URL without including the word relativity forward slash] + purview-sync-services/api/v1/AppConfiguration/auth-response. For example, https://company.relativity.one/purview-sync-services/api/v1/AppConfiguration/auth-response.

- Click Save. Exemplary added URIs look as follows.
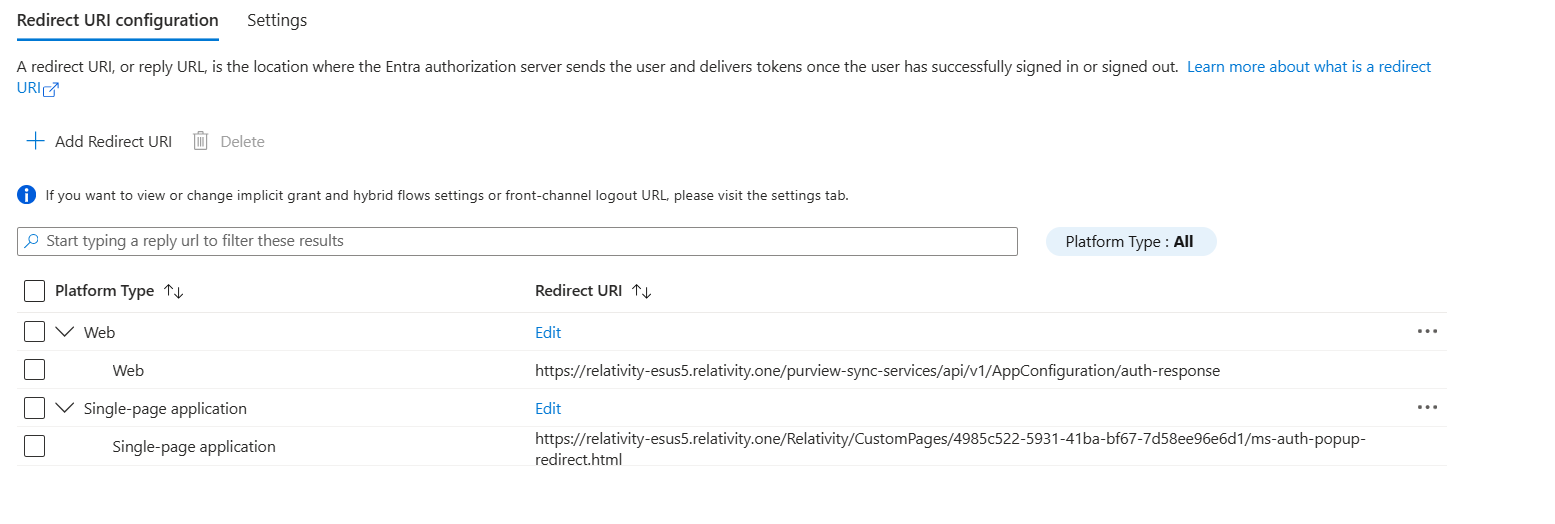
- If you plan to use the same app registration on another tenant, add another two corresponding redirect URIs—Single-page URI and Web URI—for that tenant in this section.
Creating a client secret
A client secret from Microsoft Azure AD is needed to integrate Microsoft and Relativity.
To create a client secret:
- In the left-navigation menu, click Certificates & secrets.
- Navigate to the Client secrets tab.
- Click the New Client Secret button.Do not navigate away from the page once the client secret is created.
- Populate the Description and Expires fields. You can leave the default, or recommended, values.
- Click the Add button.
If the client secret was successfully created, Microsoft will display the Client Secret on the table and the Value field in plain text. - Copy the Value field and securely store it.
Microsoft hides the Value field if you leave the page and then come back to get the value. At this point, you cannot copy it.
You can repeat steps 4-5 to generate a new client secret.
Setting API permissions
Open the application to view the application's homepage. From the application's page, add permissions to the web API.
To add permissions:
- Click API permissions.
- Click + Add a permission.
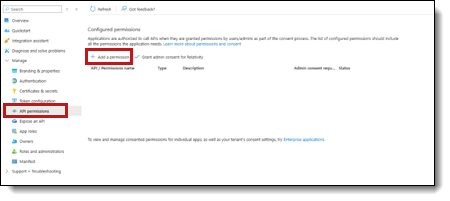
- Click Microsoft Graph.
- Select Delegated Permissions.
- Select the eDiscovery.ReadWrite.All option from the Delegated Permissions section.
- Click Add Permissions.
- Click Grant admin consent for [Tenant Name].You need the Global Administration role to complete this action.
At this point the Application should be fully configured. It can take a few minutes to update.
Create the service principal
There is a special permission not available in an application registration by default. This is the eDiscovery.Download.Read permission that allows the transfer of data. It becomes available once you create a Service Principal for your Azure tenant. For more information, see Microsoft's Service Principal documentation.
We recommend using Microsoft Graph Explorer to do this.
Before using Microsoft Graph Explorer, you need an account that has Application.ReadWrite.All permission. If you are not sure what this means, ask someone in your organization with the Global Administrator role in your Azure tenant. For more information on the required permissions, see Microsoft's Service Principals documentation.
Creating the service principal steps:
- Navigate to https://developer.microsoft.com/en-us/graph/graph-explorer.
- Click on the avatar icon on the top right.
This opens a login window, where you can login with your credentials.
- Click on the blue GET button. Select POST as the query method.
- Enter https://graph.microsoft.com/v1.0/servicePrincipals in the URI field.
- Under Request body, enter: { "appId": "b26e684c-5068-4120-a679-64a5d2c909d9" }.Do not forget the curly brackets.
- Press the Run query button.
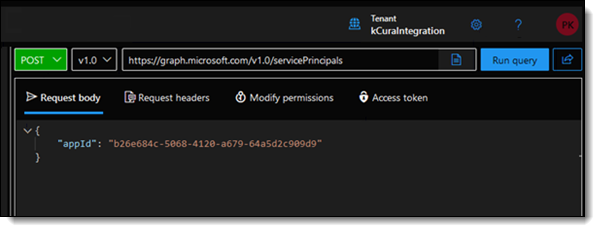
- Confirm you received a Created – 201 response.If it’s already set up, you will see a 409 error.
Configure permissions
Now you need to add the eDiscovery.Download.Read permission we made available by adding the service principal in the Create a Service Principal section. Navigate back to Microsoft Azure Portal, to the application registration you set up earlier.
- Click the API permissions in the left-hand side menu.
- Click + Add a permission.
- Select the APIs my organization uses tab.
- In the search bar, enter MicrosoftPurviewEDiscovery.
- Select the application MicrosoftPurviewEDiscovery search result.
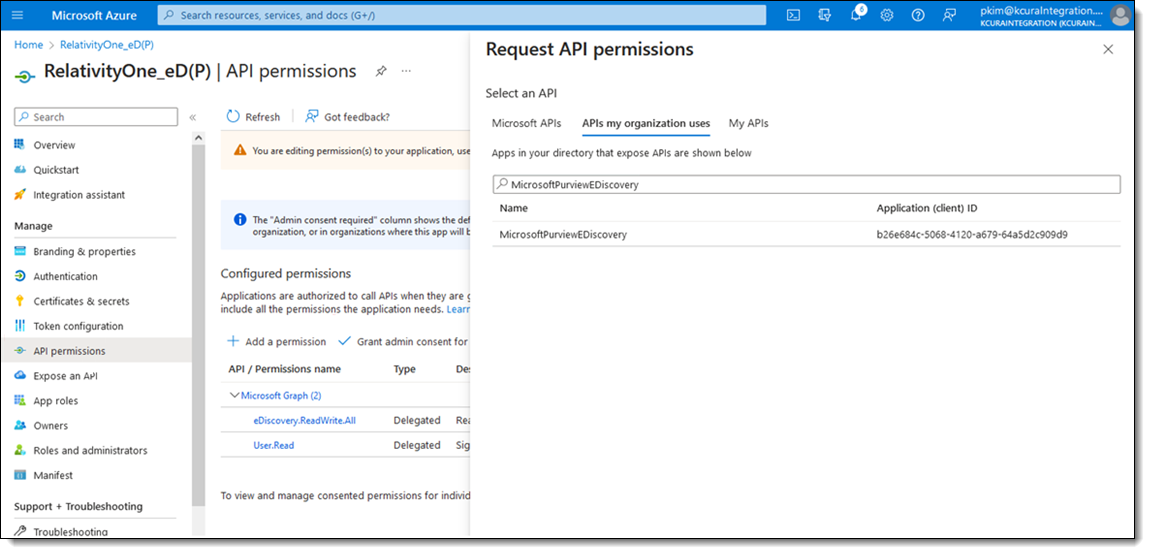
- Select the Delegated Permissions box.
- Select eDiscovery.Download.Read.
- Click Add permissions.
- Click Grant admin consent for [TENANT NAME].You need the Global Administration role to complete this action.
- In the pop-up modal that appears, click Yes.
You completed configuring the application registration with Azure. Now onto Relativity.
Grant users eDiscovery permissions in Microsoft Purview
There are two categories of permissions to use the Purview Sync app:
- Azure Active Directory roles. These roles are necessary to grant eDiscovery permissions.
- Purview eDiscovery Premium roles. These roles are necessary to execute actions in Purview eDiscovery Premium, and the Purview Sync application within RelativityOne.
Before starting, the user performing the actions in this section must have:
- Azure Active Directory role—Compliance Administrator, to be able to read, configure, and manage compliance permissions with Microsoft Purview, formerly known as Security & Compliance Center.
- Azure Active Directory role—Compliance Data Administrator, to be able to create and manage compliance content within Microsoft Purview.
Once the Compliance Administrator and Compliance Data Administrator roles have been assigned to the person configuring this user, that user will then be able to configure permissions within the Microsoft Purview compliance portal here.
If you see a screen that the Microsoft compliance portal is retired, it might mean that you are using the old Microsoft compliance portal that was disabled in November 2024. Navigate to the new Microsoft Purview instead.
Setting up Compliance Admin roles
To set up Compliance Admin roles to use Azure AD:
- Navigate to https://purview.microsoft.com and log in.
- Click Settings > Roles and scopes > Role groups.
- Click the Compliance Administrator role > Edit > Choose users.
- Ensure all users, including service accounts that will be using Purview Sync in RelativityOne, are assigned this role.
- If there are users that need to be added, click the Add assignments button to add them.
- Close the Assignments page once all the appropriate users have been added.
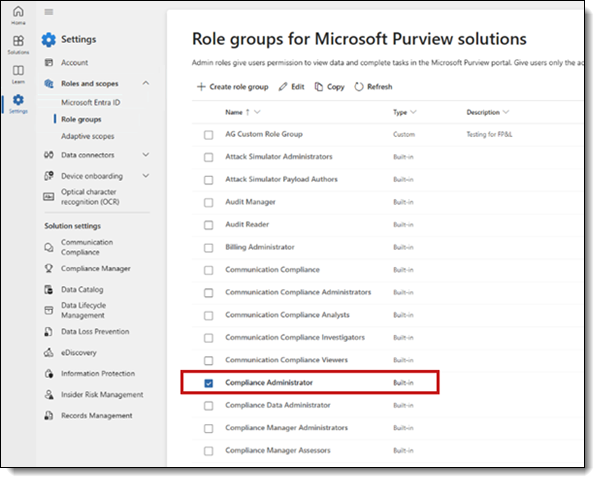
- Click the Compliance Data Administrator role > Edit > Choose users.
- Ensure all users, including service accounts that will be using Purview Sync in RelativityOne, are assigned this role.
- If there are users that need to be added, click the Add assignments button to add them.
- Close the Assignments page once all the appropriate users have been added.
Purview eDiscovery Premium Permission Management for users
- Navigate to https://purview.microsoft.com and login.
- Click Settings > Roles and scopes > Role groups under the Microsoft Purview solutions section.
- Click eDiscovery Manager.
- Select Edit.
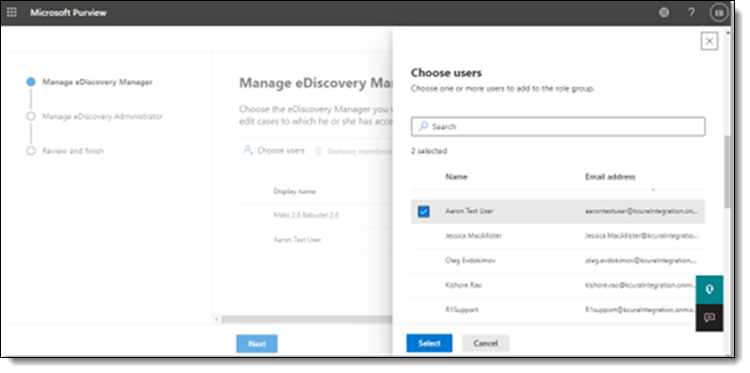
- Assign that user to the eDiscovery Manager role by following these sub-tasks if you want a user to be able create cases in Purview eDiscovery Premium, but not see other cases. If not, skip to step 6:
- Click the Choose users button.
- Select the users to add to the eDiscovery Manager role in the right-side menu.
- Click the Select button.
- Click the Next button at the bottom of the page until you navigate through Manage eDiscovery Administrator and Review and finish options.
- Click the Save button.
- If you want to allow a user the capability to create cases and see cases that other users have created, then assign that user to the eDiscovery Administrator role by following these sub-tasks, otherwise skip to the next section.
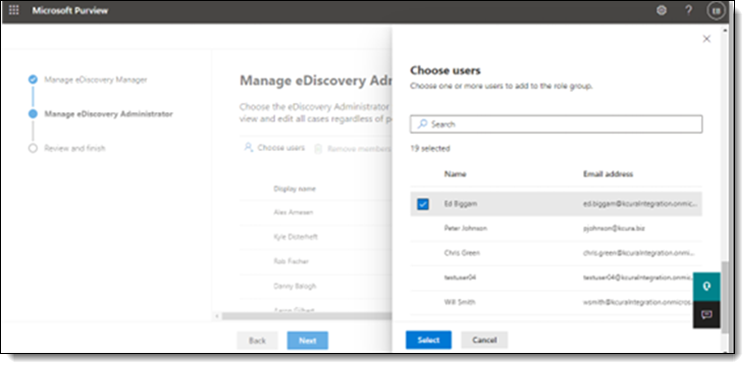
- Click the Next button to navigate to the Manage eDiscovery Administrator options.
- Click the Choose users button.
- Select the users to add to the eDiscovery Administrator role in the right-side menu.
- Click the Select button.
- Click the Save button.
You have now granted a service or user eDiscovery permissions in Microsoft Purview.







