Last date modified: 2026-Mar-05
Authentication
Relativity
Permissions
Authentication overview
Review the following sections to learn more about the authentication methods, the object model, and the permissions model supported by Relativity:
Relativity
- Password—a method that includes a user name, the user's email address, and a password.
- OpenID Connect—a protocol for an external identity provider, authenticating against an external identity provider using the OpenID Connect protocol. OpenID Connect is a modern authentication protocol can be used to connect to providers such as Microsoft Entra ID. See OpenID Connect for more information.
- SAML 2.0—a method that authenticates against an external identity provider using the SAML 2.0 protocol. SAML 2.0 is an older authentication protocol that is still in widespread use. See SAML 2.0 for more information.
- When implementing single sign-on (SSO) across Relativity instances, the following scenarios are supported:
- Identity Provider-initiated SSO using SAML 2.0
- ID provider and service provider-initiated SSO with OpenID Connect
- To log in using PIV/smartcard, configure RelativityOne with an OpenID Connect or SAML provider that supports PIV/smartcard logins. PIV/smartcards are not directly supported in RelativityOne.
In addition to the above protocols, Relativity has the following additional authentication features:
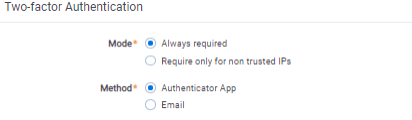
- Two-factor Authentication—when logging in with the Password method, you can require the user to pass an additional two-factor check based on an email or message sent to the user's phone, through a mobile email gateway.
- Mode—always required or require only for non-trusted IPs
- Method—Authenticator App or email. For more information, see the authenticator app's documentation.
- Trusted IP Range—limit access to the Relativity application based on the user's source IP address.
Relativity provides several tabs or object types that are used to configure authentication. By combining these object types, the system admin is able to control the Relativity login page and authentication options for the users in the environment.
Authentication Provider- Authentication Providers allow you to configure the specific settings for a login protocol. For example, you can add the Password Provider to your environment to set minimum and maximum password length, password history settings, and more. Some protocols have multiple configuration options, while others have very few. Every instance of Relativity has Default Password. You can't have additional (non-default) providers of those types.
You can add OpenID Connect and SAML 2.0 external identity providers. Unlike the previous five protocols, you can have as many of these Providers as you wish in an environment.
Login Method - Users can have one or more Login method objects that binds that user to a particular Authentication Provider. For example, if you have a Password Authentication Provider in the environment, the Password Login Method contains the specific password for a given user. If you have Azure Active Directory configured as a Provider, each user's AAD subject identifier would be stored in an associated Login method.
User. The User object still holds the TrustedIPs setting. By setting a TrustedIP for a user, that user will only be able to authenticate with Relativity from that IP range. All other authentication-related fields have been moved from the User object to the Provider and Method objects.
These default object permissions are recommended for managing user authentication:
- System admins only—full permissions, including view, update, delete, secure, add
- Authentication Provider Type
- Authentication Provider
- Login Method
- OAuth2 Clients
- Anyone with the ability to view a user—view
- Authentication Provider Type
- Authentication Provider
- Login Method
- Anyone with the ability to edit a user—update, delete, add
- Login Method
Configuring Relativity authentication
System admins must assign users at least one authentication method in order for users to log in. To create and to assign methods, follow these steps.
Authentication providers are instances of authentication provider types. You create only the instances of the provider types you need. For example, if you plan to support only password methods, you only have to create an authentication provider for passwords, and not for any other provider types.
Adding a new authentication provider of the same type overwrites the existing ones of the same type.
You may only have one instance of each provider type. The exceptions are for OpenID Provider and SAML 2.0 provided types. You can have multiple instances of those if they have different names.
To create an Authentication Provider:
- Select the Authentication Provider tab.
- Click the New Authentication Provider button.
- Enter a Name. This is the friendly name of the provider instance.
- Optionally select the Enabled status. By default, each authentication provider is enabled. If not enabled, then users can't log in with that method.
- Select a Provider Type from among the authentication provider types. You can select OpenID Connect or SAML2.
The Authentication Provider Settings section appears. - Set the Authentication Provider Settings, if any. See Authentication provider settings for the specific method.
- Click Save.
For help with error messages, please see the SSO Troubleshooting console.
You assign an authentication method to each user for them to log in with. Each user must have at least one authentication method in order for them to log in but you may assign multiple methods. See Managing user authentication methods.
Enabling RelativityOne Connect
Enable RelativityOne Connect to connect two or more of your Relativity instances. Use a single identity to securely connect multiple instances and let users navigate between them securely with cross-authentication using a single sign-on provider (SSO). For more information, see RelativityOne Connect.
Authentication provider settings
Authentication providers may have associated settings that you can configure and applies to all instances of that authentication provider.
Each provider instance has at least one setting: Enabled. If set to Yes, this authentication provider is available. If No, you can't use this method to log in with. To enable an instance both this setting and the Enabled for the Authentication Provider must be set to Yes. If either one is set to No, that method isn't available for the user.
Authentication providers that require additional settings:
- Default Password provider
 View additional settings for the Default Password provider
View additional settings for the Default Password provider
- Minimum Password Length – sets the minimum number of characters for a password.
- Maximum Password Length – sets the maximum number of characters for a password.
- Maximum Password Attempts Before Reset Required – sets the maximum number of consecutive unsuccessful login attempts before being locked out. You must send the user a password reset request before they can attempt to log in again.
- Maximum Password Age (in days) -sets the maximum number of days a password remains valid. The user will be prompted for a new password on a logon at the expiration date. If set to zero, the password does not expire.
- Users Can Change Password Default – enables the user to change their password.
- Allow Password Recovery via Email – enables the user to use email to recover a forgotten password. Yes displays the Forgot Password link on the user's login screen.
- Password Recovery Request Limit – sets the maximum number of password resets before Relativity locks out the user. You must send the user a password reset request before they can attempt to log in again. This value resets to zero on each successful log in.
- Maximum Password History – sets the maximum number of previous passwords that users can't use for a new password. The default value of zero enables any previous password.
- Additional Work Factor – increases the number of encryption hashes. Relativity already provides several built in hash levels represented by the default zero value. Changing this value to 1, 2, or 3 adds additional encryption protection but may significantly increase login time.
The following non-alpha-numeric characters are not allowed: \, ", <, >, £ in passwords.
- OpenID Connect with Microsoft Azure AD - see OpenID Connect authentication provider flows.
- SAML 2.0 provider - see SAML 2.0 provider.







