Last date modified: 2026-Mar-05
Installation and configuration
Relativity installs the Data Breach Response application at the instance level. After this initial installation, you must add the application to each workspace where you plan to use it and configure user roles and permissions.
Prerequisites
Following are prerequisites for using the Data Breach Response application:
- Data Breach Response relies on the Control Number field. This field must be populated in the Document ID data settings field mapping before ingesting documents.
- The Data Breach Response application analyzes the Extracted Text field.
- If you OCR documents, the resulting text must be stored in the Extracted Text field
- The Extracted Text field must be stored in Data Grid.
Installation to workspaces
Once Relativity installs the application at the instance-level, your team can install it into selected workspaces.
To add the application to a workspace:
- Search for and open Relativity Applications from the Quick nav.
- Click New Relativity Application.
- Click Select from Application Library.
- Search in your application library for Data Breach Response and install it in your workspace.
User roles and permissions
We recommend creating two dedicated permission groups for Data Breach Response users.
Following is a list of user roles for the Data Breach Response application and the permissions available to them.
| Role | Permissions |
|---|---|
| Data Breach Response - Lead |
Users assigned a lead role have access to all features in Data Breach Response:
|
| Data Breach Response - Annotator |
Annotators can access the following features:
|
Configure permissions
To configure the permissions groups for the Data Breach Response Application:
- From your workspace, navigate to Workspace details.
- Click Manage Workspace Permissions.
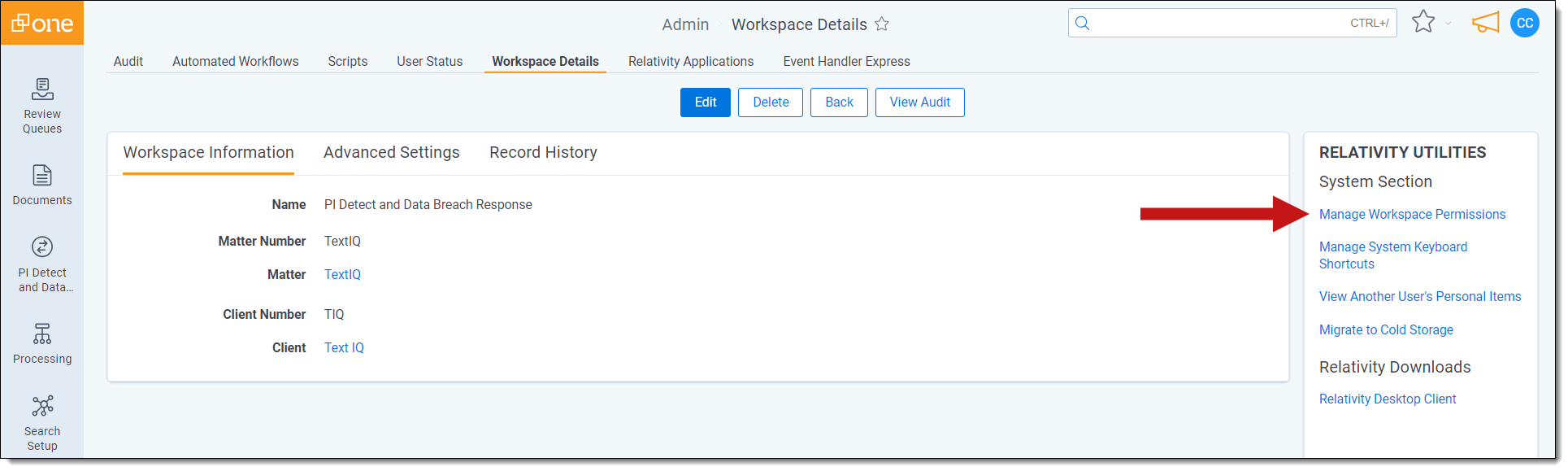
- Open the Object Security tab.
- Under Workspace, toggle on either the Lead or Annotator group as appropriate.
See User roles and permissions for details on each role. For more instructions on editing and deleting permissions, see Setting workspace permissions.
For more instructions on editing and deleting permissions, see Setting workspace permissions. - Click Save.
Set the Data Breach Response application as a default tab
Once you install the application to a workspace you can set it as a default tab:
- Click on Workspace Setup and select Tabs.
- Find the Data Breach Response application.
- Click the pencil icon to edit.
- Enable Visible under Tab Information.
- Enable Show in Sidebarunder Tab Location.
- Pick an icon.
- Click Save.
The Data Breach Response application should now be visible in the sidebar.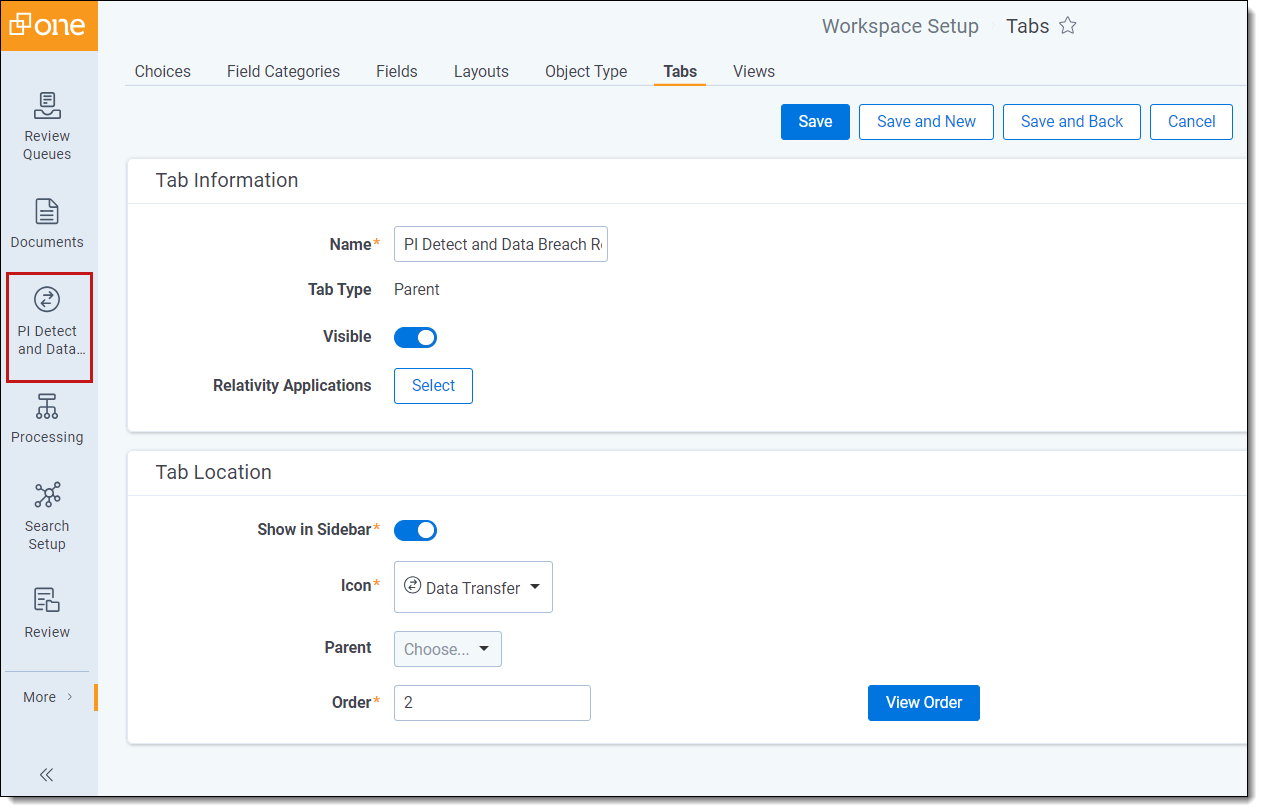
Frequently asked questions
The Privacy Workflow tab will not populate until you run an ingestion job. During the first ingestion job, the application backend prepares for the project. You can access the Privacy Workflow tab when the job completes.







