Last date modified: 2026-Mar-09
Security Alerts
The Security Alerts interface shows recent events that may impact the security of your instance. These events can be sorted, filtered, and viewed in detail in order to assess their impact. In addition, the Alert Details section provides recommended remediation steps tailored to each alert type.
See the following related pages:
Security alert types
The security events monitored and reported here are categorized into alert types. The system generates alerts on a regular schedule, so multiple alerts may display the same or similar "created" timestamps. These timestamps do not reflect the actual time of the audited action. To view the accurate audit timestamps, select the alert and review its details.
The alert types are as follows:
| Alert name | Severity level | Cause |
|---|---|---|
| EnableCustomerLockbox Instance Setting Changed | Medium | A user changed the value of the "EnableCustomerLockbox" instance setting. |
| EnableRelativityLockbox Instance Setting Changed | Medium | A user changed the value of the "EnableRelativityLockbox" instance setting. |
| Enabled User | Low | A previously disabled user account was enabled. |
| Login Method Changed | Medium | A password login method that is not 2-factor authentication (2FA) enabled was added for a user. |
| Multiple Failed Logins | Medium | Users who fail to sign in more than three times within 10 minutes trigger a multiple failed logins security alert. |
| New Login Location | Low | A user logged in from a location he or she has not previously used. |
| User Added To Group | Low | An edit was made to the System Administrator group. |
| Brute Force Login | Medium | 50 or more failed login attempts were detected within 1 hour. |
| Document Download | High | A Relativity employee downloaded a document from a workspace. |
| Client Domain alert types: | ||
| User and Group | Low |
A user has been added to a group with mismatched "Client" fields. This indicates a potential misconfiguration where a user from one client has been added to a group from another client. |
| User and Group with ROSE Permission | Critical |
A user has been added to a group with mismatching "Client" fields. This indicates a potential misconfiguration where a user from one client has been added to a group from another client. Furthermore, the group grants permissions for RelativityOne Staging Explorer, enabling users in the group to access file natives in the Staging area. |
| Group and Workspace | High |
A group has been assigned permissions to a workspace with a different "Client" field value. This indicates a potential misalignment of client domains and could allow users from one client to access workspace data of another client. |
| Workspace and Resource Pool | High |
A workspace has been configured with a resource pool belonging to a different client. This could result in the addition of client data to the workspace of another unrelated client domain. |
Client Domain alert types will only occur within RelativityOne instances with Client Domains configured.
When any of these conditions are met, members of the Security Notifications group will receive an email notification. The notification email includes a link to the Security Center where Relativity workspace access can be revoked if needed.
Alert severity levels
Each alert type is assigned a severity level which corresponds to its potential impact on system security. These levels are meant as guidelines only, and the actual impact must be determined on a case-by-case basis by an administrator.
The alert severity levels are as follows:
- Low — informational alerts. These events typically do not require any action, but we recommend investigating any unusual patterns.
- Medium — non-standard action or unusual behavior occurred. Investigate each instance and determine the impact, if any.
- High — security event with potentially high impact occurred. Investigate immediately and look for secondary impacts.
- Critical — event or sequence of events occurred that require urgent attention. Investigate immediately and alert Relativity personnel by contacting support@relativity.com.
Security alerts can be triggered by normal, non-malicious actions. Use the information on the Remediation Steps tab to help you determine whether the actions were malicious or not. For more information, see Alert Details section.
Security alert states
Efficient security alert management relies on tracking their resolution status. Newly generated alerts automatically receive the "Unresolved" state, indicating they require review. After examining an alert, you can designate its final status as either "Dismissed" or "Resolved." This clear designation allows for easy identification of addressed alerts and facilitates overall security posture maintenance.
| Alert State | Description |
|---|---|
| Unresolved | signifies an alert that hasn't been reviewed or addressed yet. System Administrators should prioritize investigating these alerts and ultimately transition them to either "Dismissed" or "Resolved" based on their findings. |
| Dismissed | indicates it has been reviewed by a System Administrator and determined not to require further action. This designation signifies the alert stemmed from an expected change or event within the system. However, the ability to revert a "Dismissed" alert back to "Unresolved" allows for additional investigation if necessary. |
| Resolved |
signifies it has been reviewed by a System Administrator and identified as a genuine issue requiring corrective action. This state indicates the triggering event wasn't an expected change but a security concern that needs to be addressed. Transitioning certain alert types to "Resolved" may trigger automated remediation workflows. In these cases, the system will take corrective actions on behalf of the System Administrator. For further details on resolving alerts and automated remediation, refer to the "Resolving Alerts and Automated Remediation" section. Additionally, even "Resolved" alerts can be reverted back to "Unresolved" if additional investigation becomes necessary. |
Dismissing Alerts
Intentional changes that have understood security impacts and do not require further action can be moved to the "Dismissed" state. To dismiss an alert, click the "Dismiss" button in the alert Summary tab or select multiple alerts and use the mass operation button to set it to "Dismiss". A confirmation window will appear to confirm the change. The alert will be moved to "Dismissed" after confirmation.
Resolving Alerts and Automated Remediation
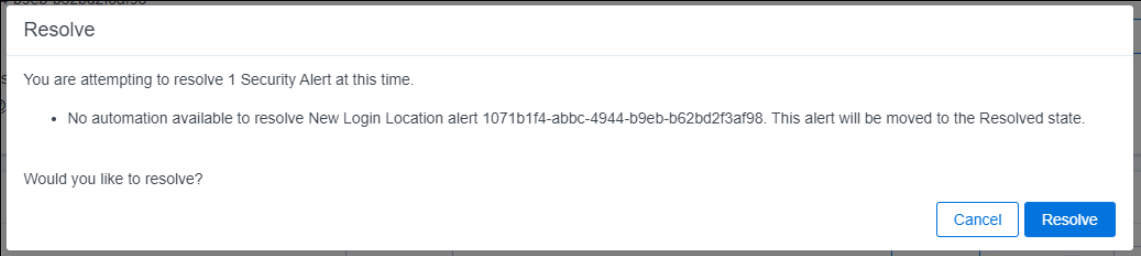
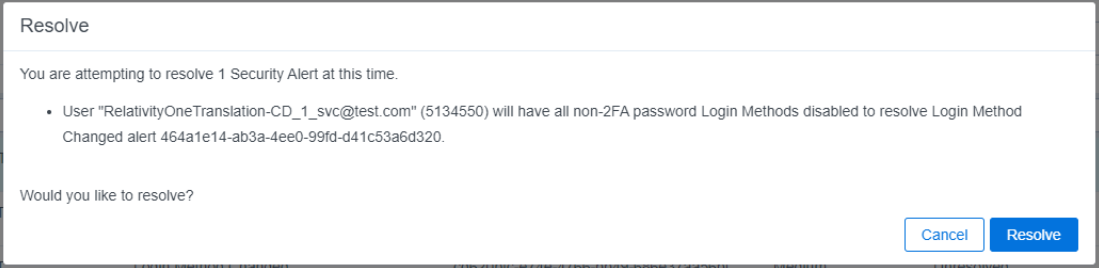
When a security alert requires system modifications to address the underlying issue, you can transition it to the "Resolved" state. Some alert types trigger automated remediation workflows that actively address the problem by implementing automated system updates. In contrast, other alerts don't have automated remediation. These require System Administrators to manually intervene and implement the necessary changes to resolve the issue. The following table provides details on alerts with automated remediation workflows, specifying the system's actions when an alert resolution is confirmed.
| Alert Types | Automated Remediation Workflow |
|---|---|
| EnableCustomerLockbox Instance Setting Changed | Reverts the value of the "EnableCustomerLockbox" instance setting to the previous value. |
| EnableRelativityLockbox Instance Setting Changed | Reverts the value of the "EnableRelativityLockbox" instance setting to the previous value. |
| Enabled User | Disables Relativity access for the user account which had Relativity access enabled. |
| Login Method Changed | Removes the Password Login Method without Two Factor Authentication that was added. |
| User Added To Group | Removes the user who was added to the Group. |
| Brute Force Login | Disable the user account which has had many failed login attempts within a short period of time. |
|
Document Download Multiple Failed Logins New Login Location Client Domain Violation - User and Group Client Domain Violation - User and Group with ROSE Permission Client Domain Violation - Group and Workspace Client Domain Violation - Workspace and Resource Pool |
No automated remediation workflows available. No system changes will be made when Resolving these alert types. |
Alerts can be moved to "Resolved" by clicking the "Resolve" button on the alert Summary tab or selecting multiple alerts and using the mass operation button set to "Resolve".
Alert type without an automated remediation workflow:
Alert type with an automated remediation workflow:
Moving Alerts back to Unresolved
To move an alert back to "Unresolved" from "Dismissed" or "Resolved," select the desired alert(s) within the Security Alerts list. Then, select the mass operation button and choose "Unresolve."
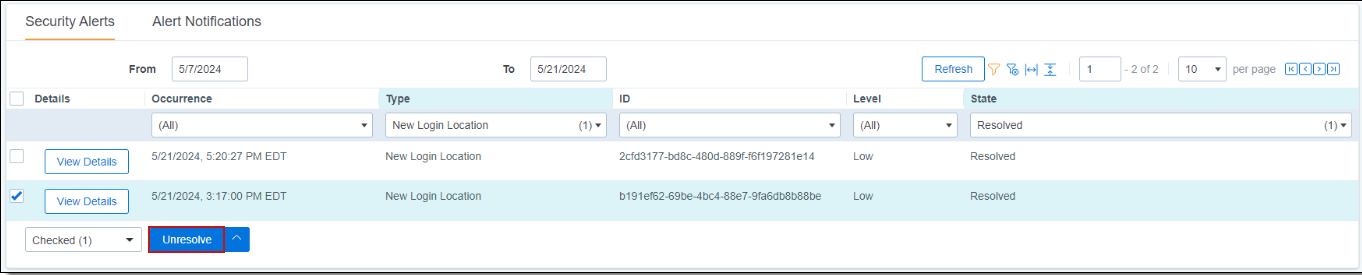
Tracking State Change History
When an alert changes states, the most recent state change history will be displayed in the alert Summary tab. This will include an update to the following fields:
| Field | Description |
|---|---|
| Current State | the state the alert is currently in |
| Last State Update | a description of who changed the alert state, and when |
| Previous State | the state the alert moved from in it's last state transition. |
| State Details | may contain more details about how the alert state change occurred. |
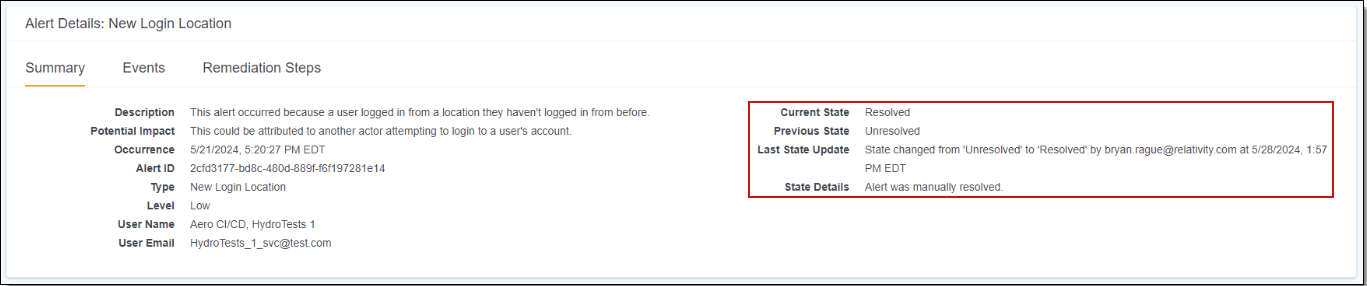
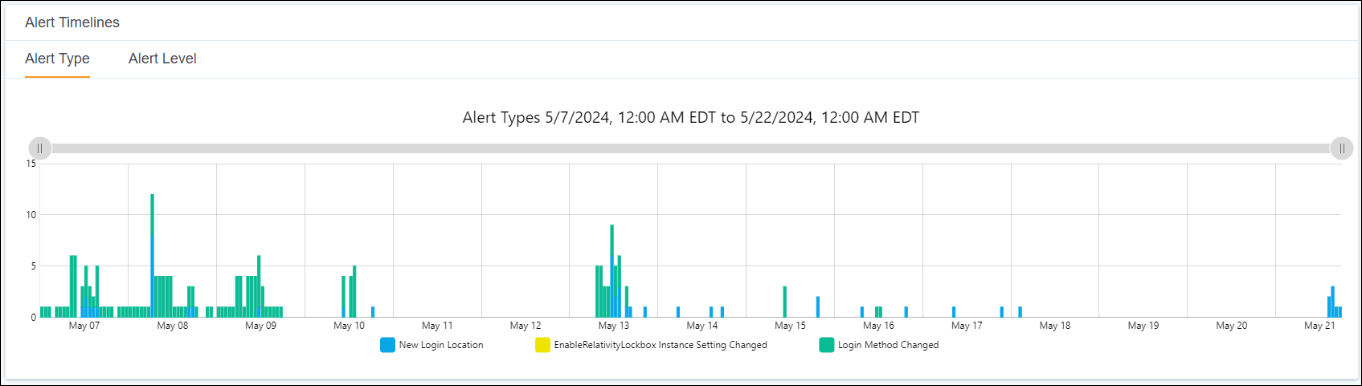
Alert Timelines section
The Alert Timelines section contains a pair of graphs showing the volume of recent security alerts. The horizontal axis shows the dates and times, with each mark representing one hour. The vertical axis shows the number of alerts. The color of the bars on the graph represents either the alert type or the alert level. Hovering over a colored section on any bar shows the time and the number of alerts generated for that category within that hour.
By default, the time frame represented in the graph is one week leading up to today's date. To display alerts from a different date range, change the date range in the Security Alerts grid below. For more information, see Adjusting the date range.
Alert Type and Level graph
The Alert Type graph shows different colors for different types of alerts. This is the first graph you see when you open the page. You can use your mouse to move and adjust the graph to zoom in or out.
- For a list of all possible alert types, see Security alert types.
- For a list of all possible levels, see Alert severity levels.
Alert Details section
The Alert Details section is designed to help you evaluate the impact of each alert and take further steps as needed. The information is broken into three tabs: Summary, Events, and Remediation Steps.
When the interface first loads, this section will show details for the first item in the Security Alerts grid below. To view details for a different alert, click the View Details button beside that alert. For more information, see the Security Alerts grid.
Summary tab
The Summary tab displays the following information:
- Description — the reason the alert occurred.
- Potential Impact — the risk associated with this type of alert.
- Occurrence — date and time of the alert.
- Alert ID — unique ID generated for this alert.
- Type — the category of alert. For a list of types, see Security alert types.
- Level — the severity level of this type of alert. For a list of severity levels, see Alert severity levels.
- User Name — the name of the user associated with the actions taken.
- User Email — the email address of the user associated with the actions taken.
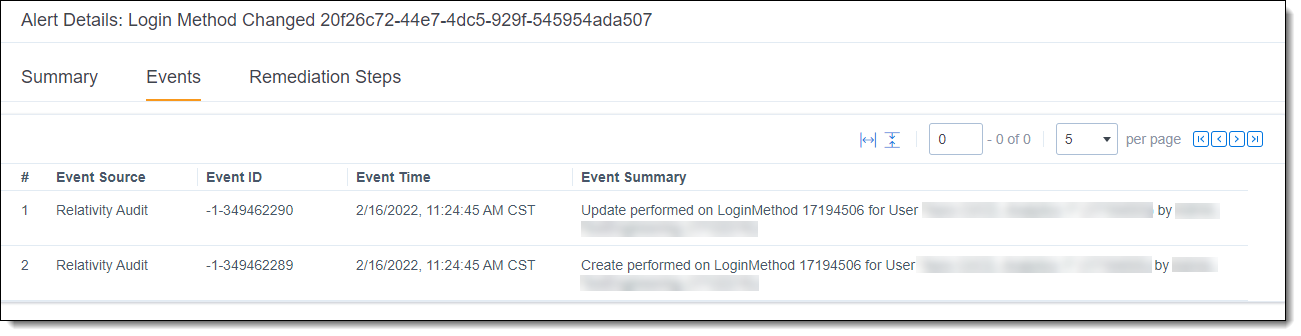
Events tab
The Events tab lists the events that are included in the selected alert. The Event Summary shows a brief description of what happened during each event, and the Event ID corresponds to the Audit ID of that action in the Audit application. More comprehensive detail about each event can be found by navigating to Audit and searching for the Event ID in the audit list. For more information, see
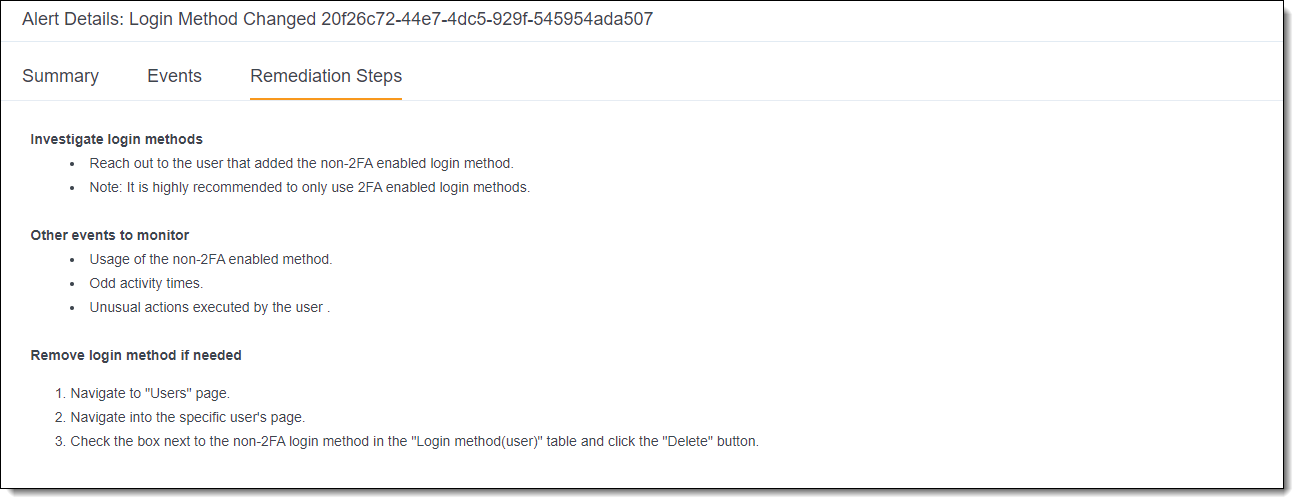
Remediation Steps tab
The Remediation Steps tab shows three categories of information: how to investigate the alert, related events to monitor, and steps for undoing or remediating the event actions if needed. These steps will be different for each alert type.
For an example of remediation steps, click the screenshot below.
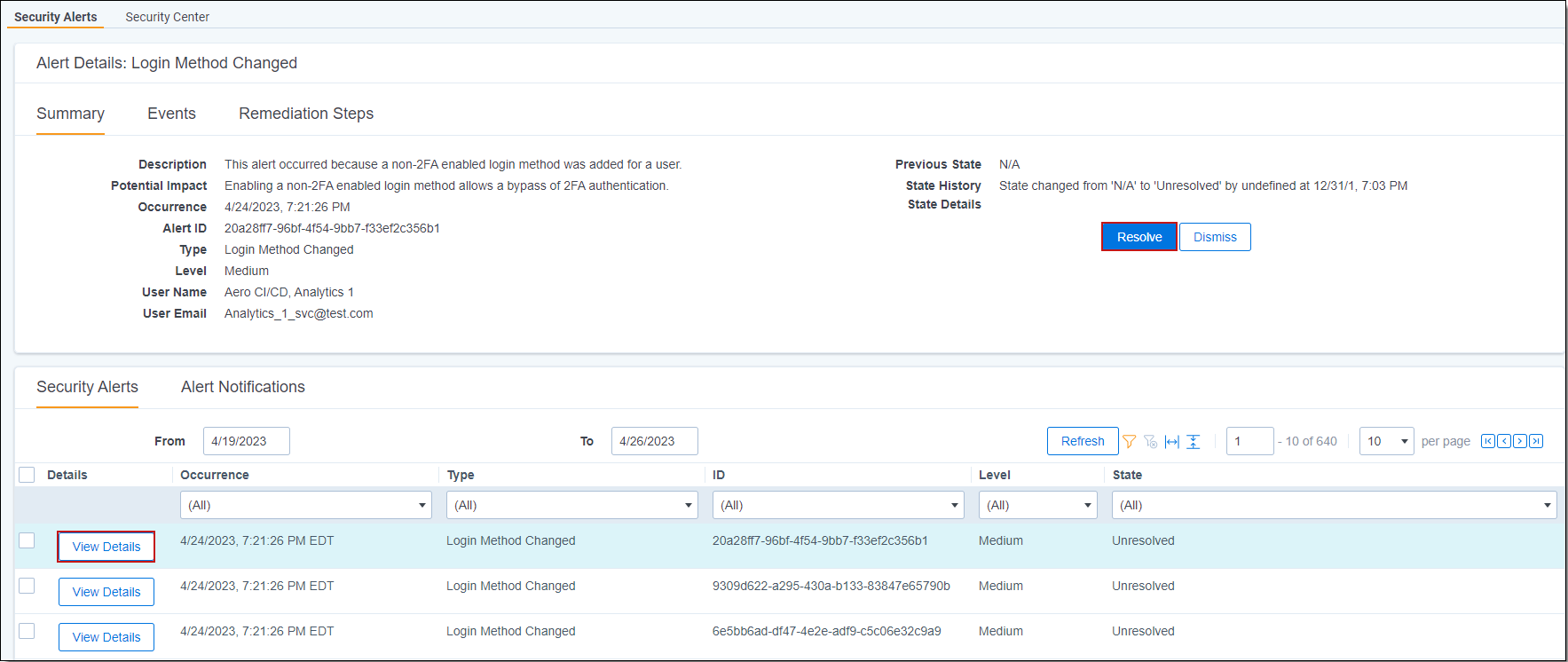
Security Alerts grid
The Security Alerts grid is an essential tool for managing and resolving security alerts. Flexible filtering options and easy-to-use interface allows you to quickly identify and address security issues to ensure the safety and integrity of your data.
The Security Alerts grid displays all alerts generated within the selected date range, with the default view showing alerts from the previous week. You can filter the grid by the following:
- Time of occurrence
- Alert type
- Unique alert ID
- Severity level
- Alert state
Additionally, clicking on any colored segment in the Alert Timelines graphs above will filter the grid to show only alerts of that type or severity level. Click Refresh to reload all alert data and remove filters.
To view details, events, and remediation steps for a specific alert, click View Details. This will display the Alert Details section, which provides relevant information about the alert. Resolutions can be addressed with a single click, while informational alerts can easily be dismissed.
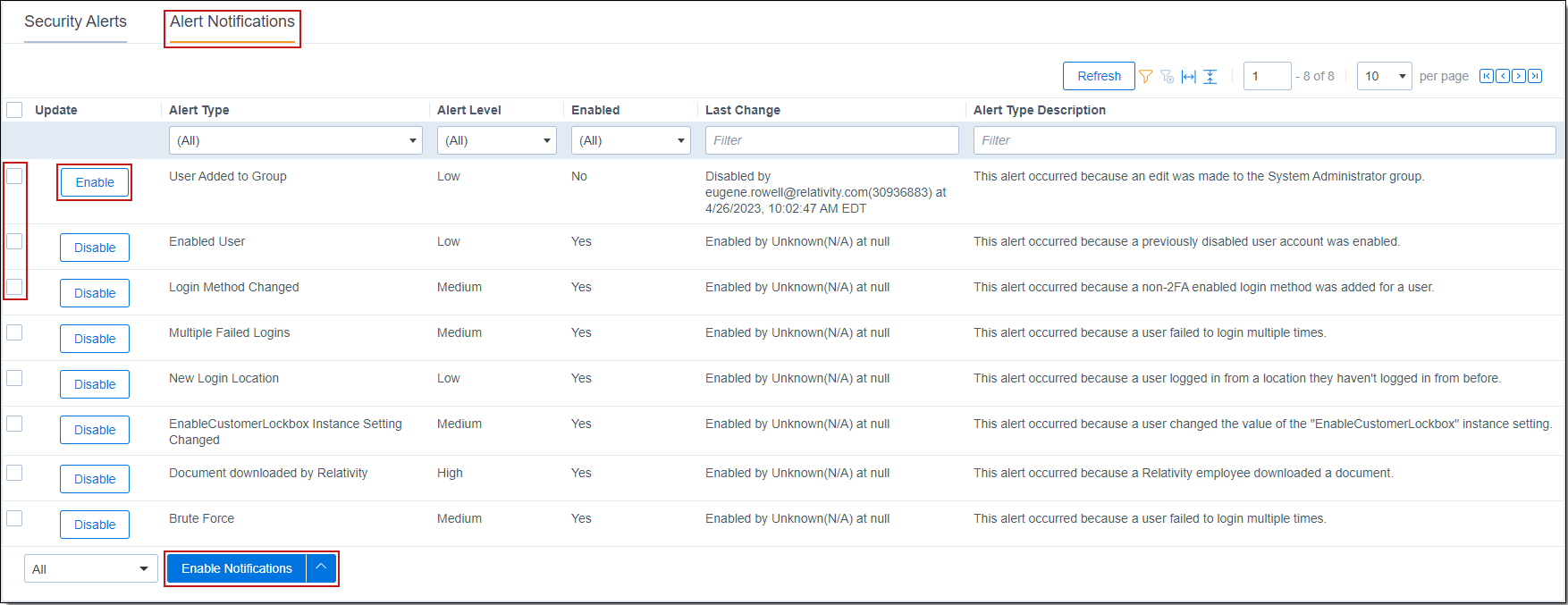
Alert Notifications tab
The Alert Notification tab allows you to easily enable or disable alert types individually, grouped, or all at once. All alerts are enabled by default.
Adjusting the date range
To specify a date range other than the previous week, enter a new date in either the From or the To field, then click Refresh. The new date range will be reflected in the Alert Timelines graphs as well as the Security Alerts grid.








