User administration
To enable access to the PI Detect and Data Breach Response application directly from Relativity:
Note: Permissions for the PI Detect and Data Breach Response application cannot be applied to the Workspace Admin group. You must create a group in Relativity and add users to that group in order to apply the permissions mentioned below. We recommend creating different groups for each permission level. For example, a PI Detect FLR group for all users assigned the PI Detect and Data Breach Response - FLR permission. See Creating and editing groups and Add users to groups for more details.
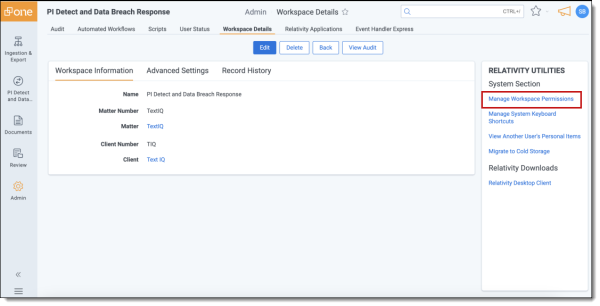
- From your workspace, navigate to Workspace details.
- Click Manage Workspace Permissions.
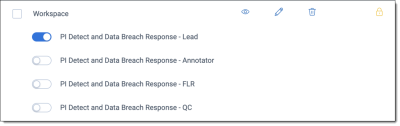
- Add user permissions.
Under object security, assign the group a PI Detect and Data Breach Response workspace permission. See PI Detect and Data Breach Response permission options for more details. - Click Save.
- After an ingestion job is run for the first time, the content in the Privacy Workflow tab will appear and provide access to the following options.
Note: Prior to running ingestion for the first time, the Privacy Workflow tab will be blank. See Ingest documents for more information.
PI Detect and Data Breach Response permission options
Following are all user roles and permissions available for PI Detect.
| Role | Permissions |
|---|---|
| PI Detect and Data Breach Response - Lead |
Users assigned a lead role have access to all features in PI Detect and Data Breach Response:
|
| PI Detect and Data Breach Response - Annotator |
Annotators can access the following features:
|
| PI Detect and Data Breach Response - FLR |
First level reviewers can access the following features:
|
| PI Detect and Data Breach Response - QC |
Quality control reviewers can access the following features:
|
Establishing project lead permissions
Users assigned a lead role have access to all features in PI Detect and Data Breach Response. To set permissions for project leads:
- Create a user group for project leads.
- Add users who you want to have lead-level access to the group.
- Navigate to the project workspace.
- Click the Administration tab and select Workspace Details.
- Click Manage Workspace Permissions to open the Workspace Security dialog.
- Select the group for your project leads to edit permissions.
- Select the Object Security tab.
- Select View, Edit, Add, and Delete for Document Centric Report and Document Centric Report Row.
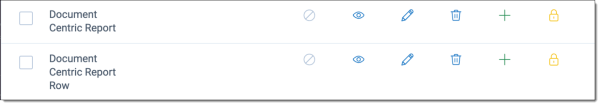
- Select View, Edit, Add, and Delete for all options starting with "PI."

- Select all options under Redact.

- Select PI Detect and Data Breach Response - Lead as the access level.Note: A user can only have one permission level at a time. Therefore, they cannot be in two user groups with conflicting permission levels.
- Select the Tab Visibility tab.
- Select all options under PI Detect and Data Breach Response.
 Note: For user groups that you do not want to run ingestion or report jobs, deselect the Jobs, Batches, Data Settings, and Configuration tabs.
Note: For user groups that you do not want to run ingestion or report jobs, deselect the Jobs, Batches, Data Settings, and Configuration tabs.